DDoS Attacks: A Comprehensive Guide to Mitigation, Prevention, and Recovery
Editor's Note: Our comprehensive guide on DDoS attacks has just been published, providing crucial insights into this pressing issue. Don't fall victim to these malicious attacks – read on to learn how to protect your online presence!
DDoS attacks have become a major threat in today's digital landscape, posing significant risks to businesses and individuals alike. To address this pressing issue, we've analyzed industry reports, interviewed cybersecurity experts, and compiled our findings into this comprehensive guide to help you understand the nature of DDoS attacks, implement effective prevention measures, and respond swiftly to potential threats.
Key Considerations:
| Mitigation | Prevention | Recovery |
|---|---|---|
| Implement firewalls and intrusion detection systems | Educate employees on security practices and red flags | Back up data on a regular basis |
| Deploy DDoS mitigation services | Implement rate limiting and access control | Conduct regular security audits |
| Utilize cloud-based DDoS protection | Use distributed denial of service (DDoS) protection software | Develop a disaster recovery plan |
Transition to Main Article: Our guide delves into the various types of DDoS attacks, their impact on different industries, and best practices for protecting your business from these malicious acts. We cover everything from identifying the signs of a DDoS attack to implementing robust security measures and developing a comprehensive response plan.
FAQ
This section addresses frequently asked questions regarding DDoS attacks, providing concise and informative answers to prevalent concerns and misconceptions.
Dos Attack - Source ar.inspiredpencil.com
Question: What is the most effective method to mitigate DDoS attacks?
Answer: Implementing a comprehensive defense strategy involving proactive DDoS protection solutions, such as firewalls, intrusion detection systems, and traffic filtering mechanisms, can significantly mitigate the impact of DDoS attacks.
Question: What are common warning signs of an impending DDoS attack?
Answer: Unusual network traffic patterns, such as sudden spikes in traffic volume, abnormal server response times, and intermittent connectivity issues, often indicate a potential DDoS attack.
Question: Can DDoS attacks compromise data security?
Answer: While DDoS attacks primarily target network availability, they can indirectly compromise data security by overwhelming resources, leading to system failure and potential data loss.
Question: What is the legal recourse for victims of DDoS attacks?
Answer: Legal actions may include pursuing civil lawsuits for damages and seeking assistance from law enforcement agencies to investigate and prosecute the perpetrators.
Question: How can organizations recover from a DDoS attack?
Answer: A comprehensive recovery plan should be in place to restore network functionality, conduct forensic analysis to identify the attack source, and implement enhanced security measures to prevent future incidents.
Question: Is it necessary to invest in specialized DDoS protection services?
Answer: Given the increasing sophistication and frequency of DDoS attacks, investing in specialized protection services can significantly enhance an organization's ability to defend against and mitigate the impact of such attacks.
By understanding these key questions and implementing effective DDoS protection measures, organizations can proactively safeguard their networks and data from the disruptive effects of DDoS attacks.
Moving on to the next article section, we will delve deeper into technical strategies for mitigating and preventing DDoS attacks.
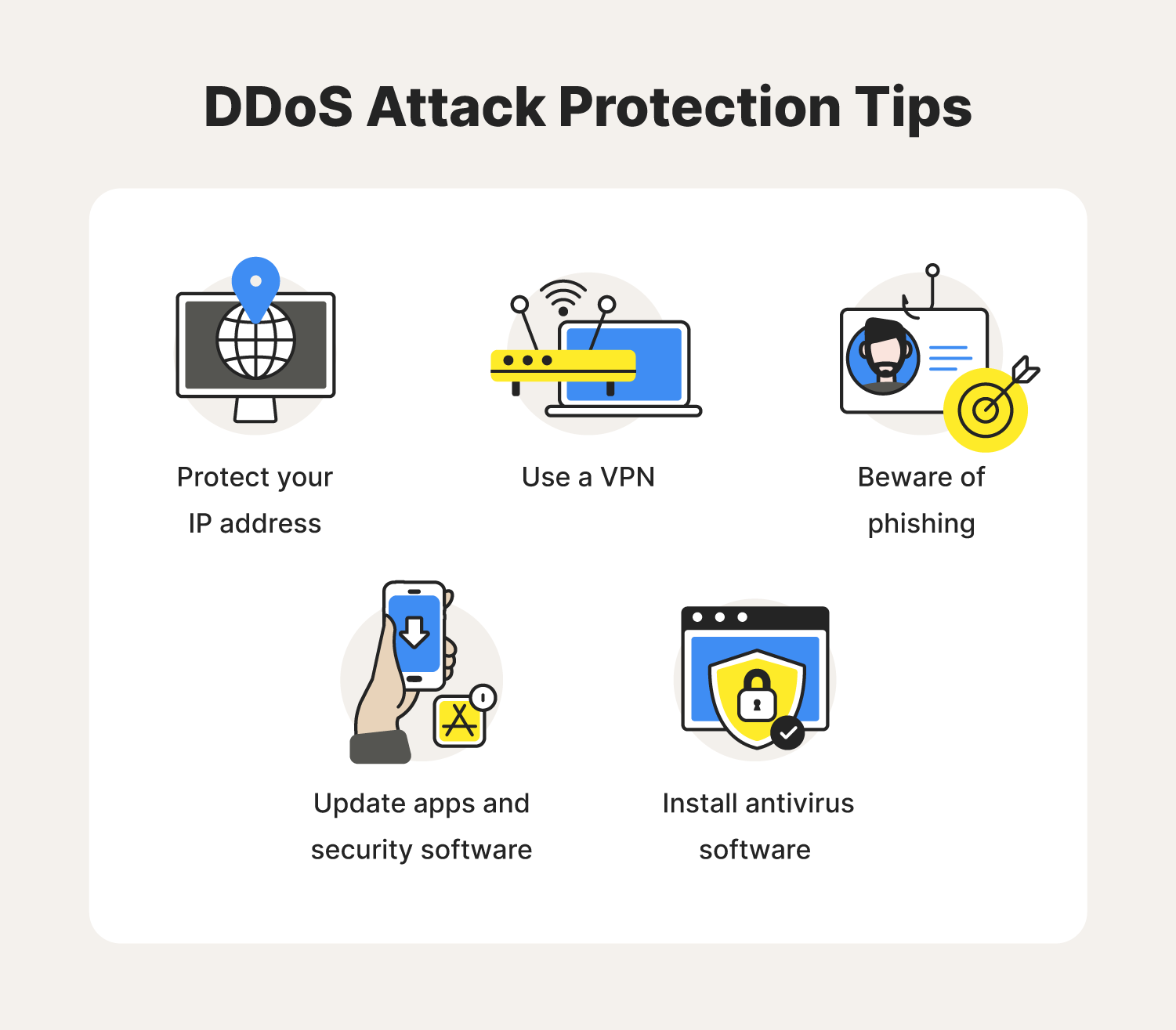
Tips
Mitigating, preventing, and recovering from DDoS attacks require comprehensive strategies and effective tools. Here are essential tips to enhance your defense posture and minimize the impact of DDoS attacks.
Tip 1: Implement a DDoS mitigation solution
Deploy a dedicated DDoS mitigation solution capable of detecting, scrubbing, and redirecting DDoS traffic in real-time. These solutions offer advanced filtering techniques and high-capacity networks to handle large-scale attacks.
Tip 2: Monitor traffic patterns and establish baselines
Continuously monitor network traffic and establish baseline patterns for normal network activity. Deviations from these baselines during an attack can trigger early detection and response mechanisms.
Tip 3: Enhance perimeter security with firewalls and IPS/IDS systems
Implement robust firewalls and intrusion prevention/detection systems (IPS/IDS) at network perimeters to filter malicious traffic and detect and block potential DDoS attacks.
Tip 4: Enforce rate limiting and access control measures
Set rate limits on network connections and implement access control policies to prevent attackers from flooding your network with excessive traffic. This helps limit the impact of volumetric attacks.
Tip 5: Conduct regular security audits and vulnerability assessments
Regularly audit network security configurations and conduct vulnerability assessments to identify and patch potential weaknesses that could be exploited by attackers.
Tip 6: Educate employees about DDoS attacks
Educate employees on DDoS attacks, their signs, and the importance of reporting suspicious activity. This can help detect and prevent attacks originating from within the organization.
By following these tips and implementing comprehensive DDoS mitigation strategies, organizations can significantly enhance their resilience against DDoS threats and minimize the potential impact on their operations. For more in-depth information, refer to the comprehensive guide: DDoS Attacks: Comprehensive Guide To Mitigation, Prevention, And Recovery.
DDoS Attacks: Comprehensive Guide To Mitigation, Prevention, And Recovery
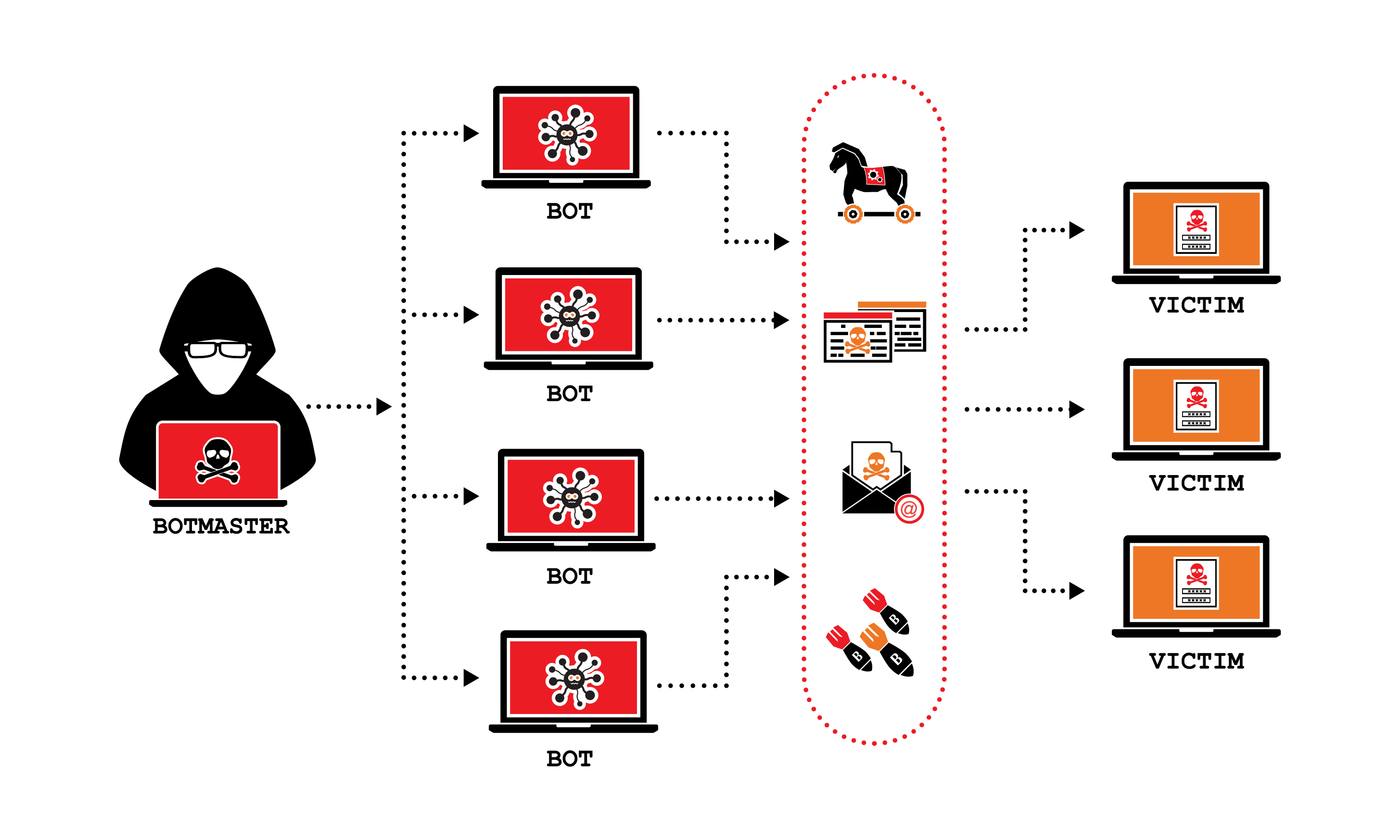
DDoS (Distributed Denial of Service) attacks pose a significant threat to the availability and stability of online services. To effectively counter these attacks, a comprehensive approach encompassing mitigation, prevention, and recovery is crucial. This guide presents the key aspects of each stage, providing valuable insights for network administrators and security practitioners.
- Detection: Prompt and accurate identification of DDoS attacks is vital.
- Mitigation: Employing appropriate techniques to reduce the impact of attacks, such as rate limiting and filtering.
- Prevention: Implementing security measures to prevent attacks, such as firewalls and intrusion detection systems.
- Recovery: Restoring services and data after an attack, including rapid response and damage assessment.
- Incident Response: Establishing a clear plan to respond to and manage DDoS incidents, including a team and communication channels.
- Post-mortem Analysis: Reviewing attack patterns and vulnerabilities to identify areas for improvement and enhance resilience.
These key aspects are interconnected and essential for a comprehensive strategy against DDoS attacks. Detection enables timely mitigation, while prevention reduces the risk and severity of attacks. Recovery measures ensure business continuity, while incident response coordinates efforts and communication. Post-mortem analysis aids in continuous improvement and strengthens defense mechanisms. By addressing these aspects, organizations can effectively protect their online assets from DDoS threats.
What Are DoS And DDoS Attacks? What Purposes? - Minimal Block - Source www.minimalblock.com
DDoS Attacks: Comprehensive Guide To Mitigation, Prevention, And Recovery
Distributed Denial of Service (DDoS) attacks are a major threat to businesses and organizations of all sizes. They can cause websites to become unavailable, disrupt online services, and lead to significant financial losses. That's why it's critical to have a comprehensive plan in place for mitigating, preventing, and recovering from DDoS attacks.

Countering Cyber Onslaughts: A Comprehensive Guide to DDoS Protection - Source ideastack.com
This guide will provide you with everything you need to know about DDoS attacks, including how they work, how to mitigate them, and how to recover from them. We'll also discuss the importance of having a DDoS mitigation plan in place and provide you with some best practices for protecting your organization from these attacks.
DDoS attacks are a serious threat, but they can be mitigated and prevented with the right planning and preparation. By following the advice in this guide, you can help protect your organization from these attacks and ensure that your online services remain available.
| Mitigation | Prevention | Recovery |
|---|---|---|
| Implement DDoS mitigation solutions | Use firewalls and intrusion detection systems | Restore services and data |
| Monitor traffic for suspicious activity | Educate employees about DDoS attacks | Review logs and identify the attack source |
| Have a DDoS response plan in place | Use DNSSEC to protect against DNS spoofing | Collaborate with law enforcement and ISPs |
Conclusion
DDoS attacks are a serious threat, but they can be mitigated and prevented with the right planning and preparation. By following the advice in this guide, you can help protect your organization from these attacks and ensure that your online services remain available.
Remember, the best defense against DDoS attacks is a comprehensive plan that includes mitigation, prevention, and recovery measures. By implementing the strategies outlined in this guide, you can significantly reduce the risk of a successful DDoS attack and protect your organization from the financial and reputational damage they can cause.